Key stakeholders and business roles in Application Portfolio Management
Business roles from both business and IT are involved in APM.
Enterprise architect
The enterprise architect is responsible for documenting and regularly evaluating applications . With the participation of other stakeholders, he/she determines what information is to be collected about the applications and by whom it is to be documented. He/she prepares the evaluation results and is responsible for the evaluation of the portfolio and ensures that potential improvements are documented, evaluated and prioritized in the form of requirements.
Business unit architects
Business unit architects take over the tasks of enterprise architects, especially in larger companies, and work closely with them. They coordinate the collection and evaluation of applications and the processing of requirements for their division, ideally for one or more strategic capabilities.
Application owners
Application owners have primary responsibility over the applications they’re in charge of. This business role corresponds to that of the service manager, which is widely known from the IT Infrastructure Library (ITIL)3. Application owners ensure that service level agreements are adhered to. They act as mediators between the business unit, IT operations and development teams. They are also responsible for documenting the applications for which they are responsible. This role is often split into a person responsible from a business perspective and one from a technical perspective, whereby it is important to ensure that the responsibilities are precisely defined.
Employees from the business departments or IT operations managers
Employees from the business departments may provide support in describing the application services. IT operations managers often provide support, particularly in the assignment of the application to the underlying system software and the IT infrastructure components.
Chief Information Officers
Chief Information Officers (CIOs) are primarily the recipients of information. They take the lead in determining which area is to be assessed as part of APM. They provide guidance on the selection of criteria to be assessed on a regular basis. Based on the results presented to them, they have to decide – supported by the enterprise architects – which measures to derive. They define in which cases proposals for transformation projects shall be made.
Chief Digital Officer
Increasingly, the role of a CDO (Chief Digital Officer) is also found in many companies. Ideally, they work closely with CIOs and enterprise architects. Together, they drive the digital transformation of the company. CDOs are responsible for innovative projects and transformation plans and coordinate the necessary organizational change. They ensure that the changes made necessary by digitalization are aligned with the operational business, customers, suppliers and products4.
Other users of the applications
Not to forget the users of the applications, whether they are employees of the organization or customers who use them. Especially when redesigning applications and application services, future users must be involved. In the case of existing applications, user behavior is ideally analysed so that potential improvements can be taken into account directly.
Application Portfolio Management approach
APM can be described as a cyclical procedure model that can be roughly divided into four steps. The steps do not necessarily have to be processed in the order suggested here. In some cases, they also run in parallel:
Record
In the first step, applications must be recorded with the most necessary properties. Here, it is recommended to limit the amount of information to the most essential attributes. Less is more! To capture the applications, an enterprise architecture tool such as our leading enterprise architecture suite ADOIT can be used.
Evaluate
Afterwards, the applications can be evaluated. Here, the criteria to be assessed, such as business or IT fitness, must be defined. The evaluation itself can then be done with the help of questionnaires. The result of this is an application’s investment strategy. If you would like to read more on the topic of APM investment strategy or application portfolio assessment, we recommend reading our related blog posts.
Identify
Based on this assessment and the defined investment strategy, improvement potentials can be identified and analyzed.
Derive measures
Last but not least, concrete measures can be derived based on the insights from previous steps.
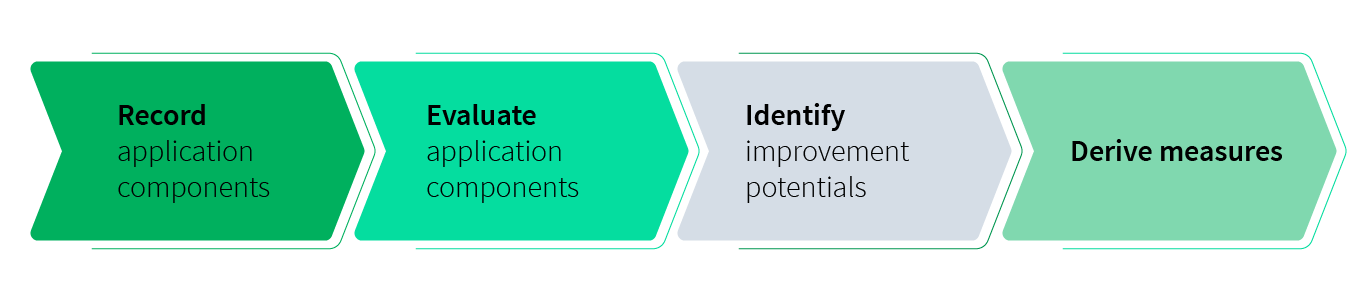
Cyclic APM Procedure Model
Just a few years ago, a common recommendation was to perform annual APM cycles. Today, this no longer seems fitting. In particular, innovative applications, which are characterized by short development cycles so that companies can react quickly to changing market needs, would not even be considered in APM. It is therefore advisable to understand APM as a continuous process, which can have an impact on the investment strategy of the application portfolio.
Key inputs are existing documentation on applications, e.g. in the form of tables, application manuals (text document) or in an EA tool. Key results are the evaluated applications, identified weaknesses and optimization potentials, and the resulting requirements and measures. These in turn trigger transformation projects or are taken into account in ongoing transformation projects.
Typical Application Portfolio Management (APM) results
The central result of APM is the application portfolio. This represents the repository of all current and future applications of the company and should be accessible to everyone in the company. The application portfolio can be evaluated using simple search and filter options.
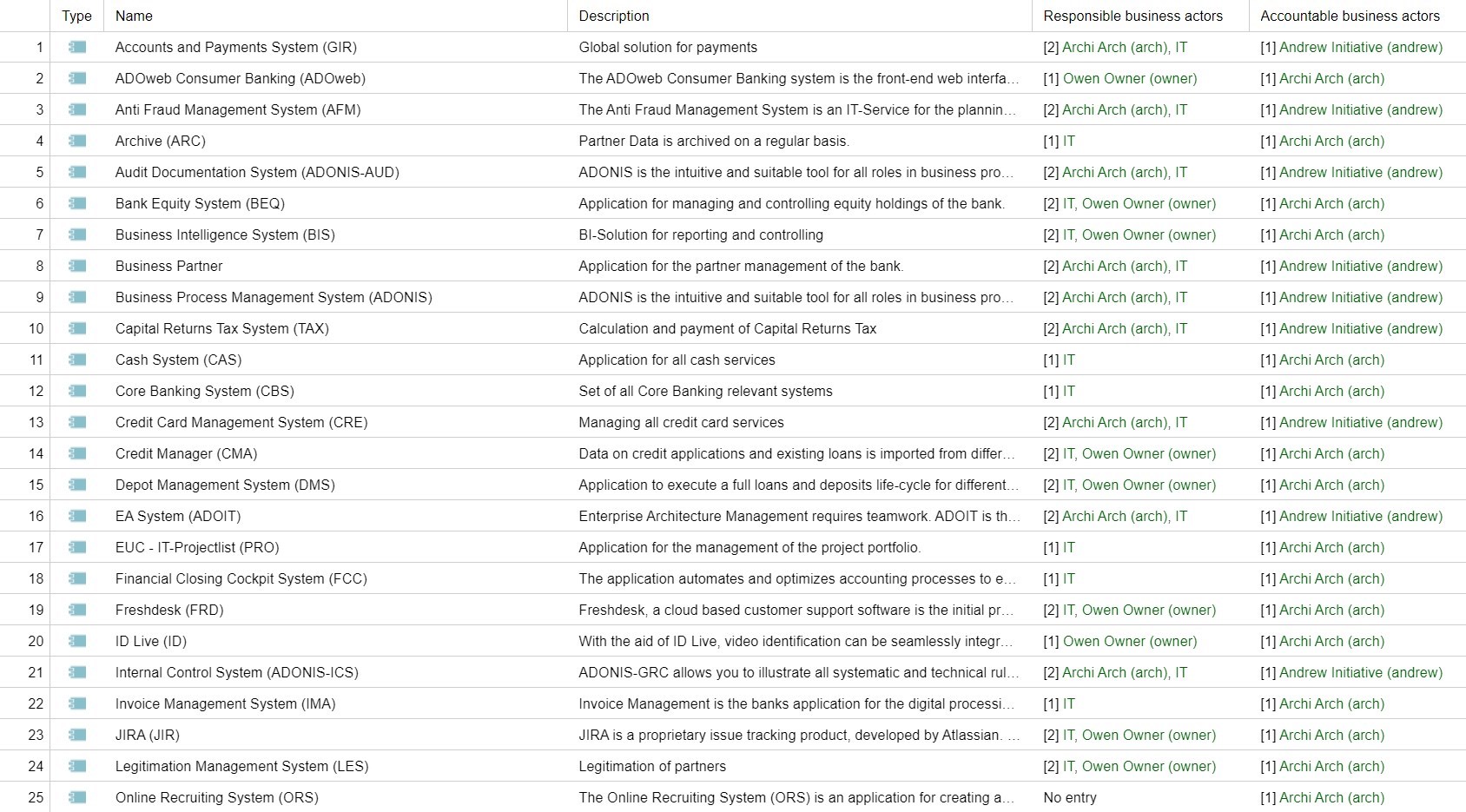
Example of an application portfolio in the EA suite ADOIT
A time-related view of the application portfolio is often particularly interesting. For transformation projects, it is important to understand how long an application will be in use and when new versions can be expected.
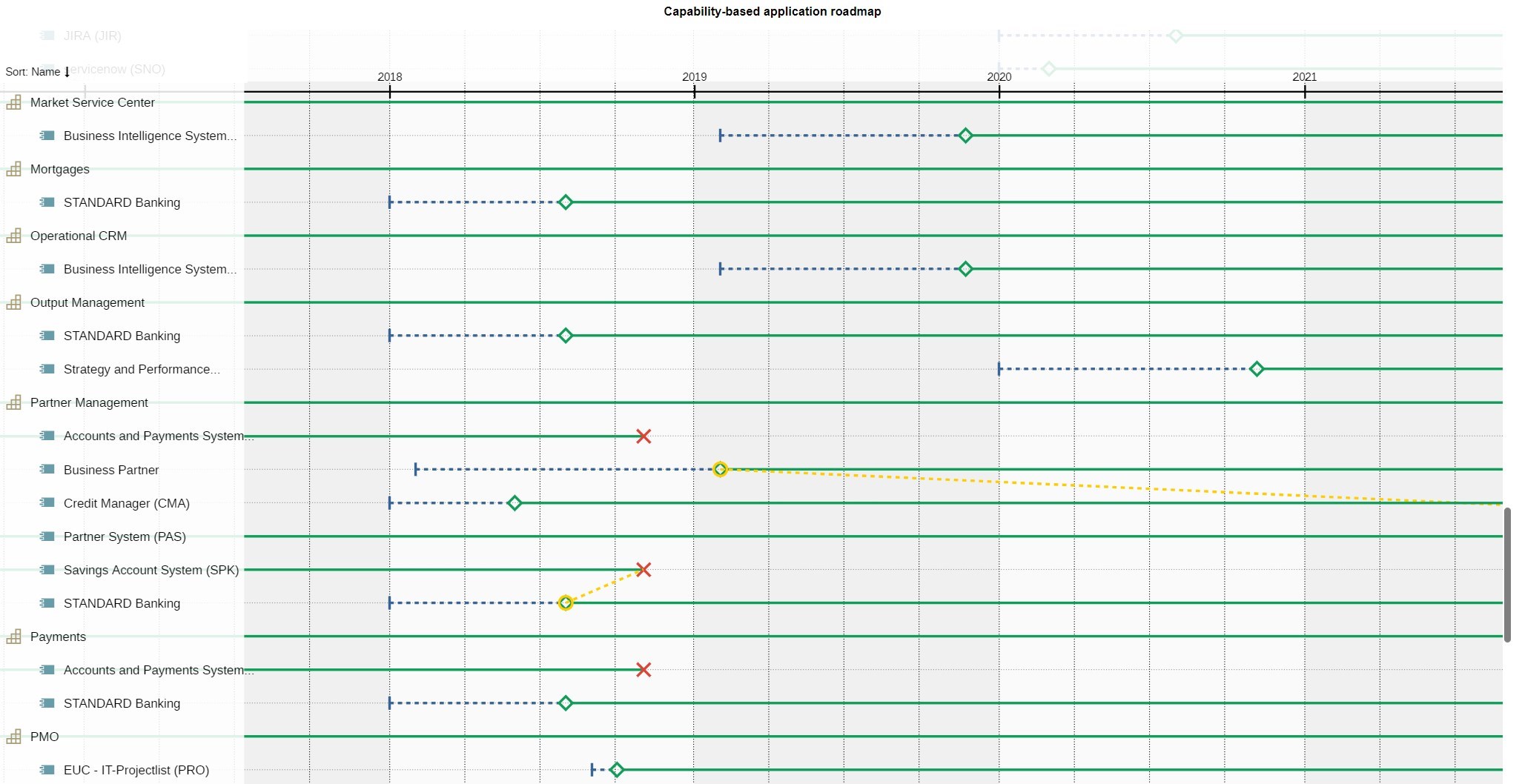
Example of an application roadmap in the EA suite ADOIT
We refer to this as the application roadmap. In this figure, the applications are grouped according to strategic capabilities.
Reports such as the dependency chart are useful for analysing the environment of an architecture element. Such representations show applications and their dependencies within the business and technology architecture.
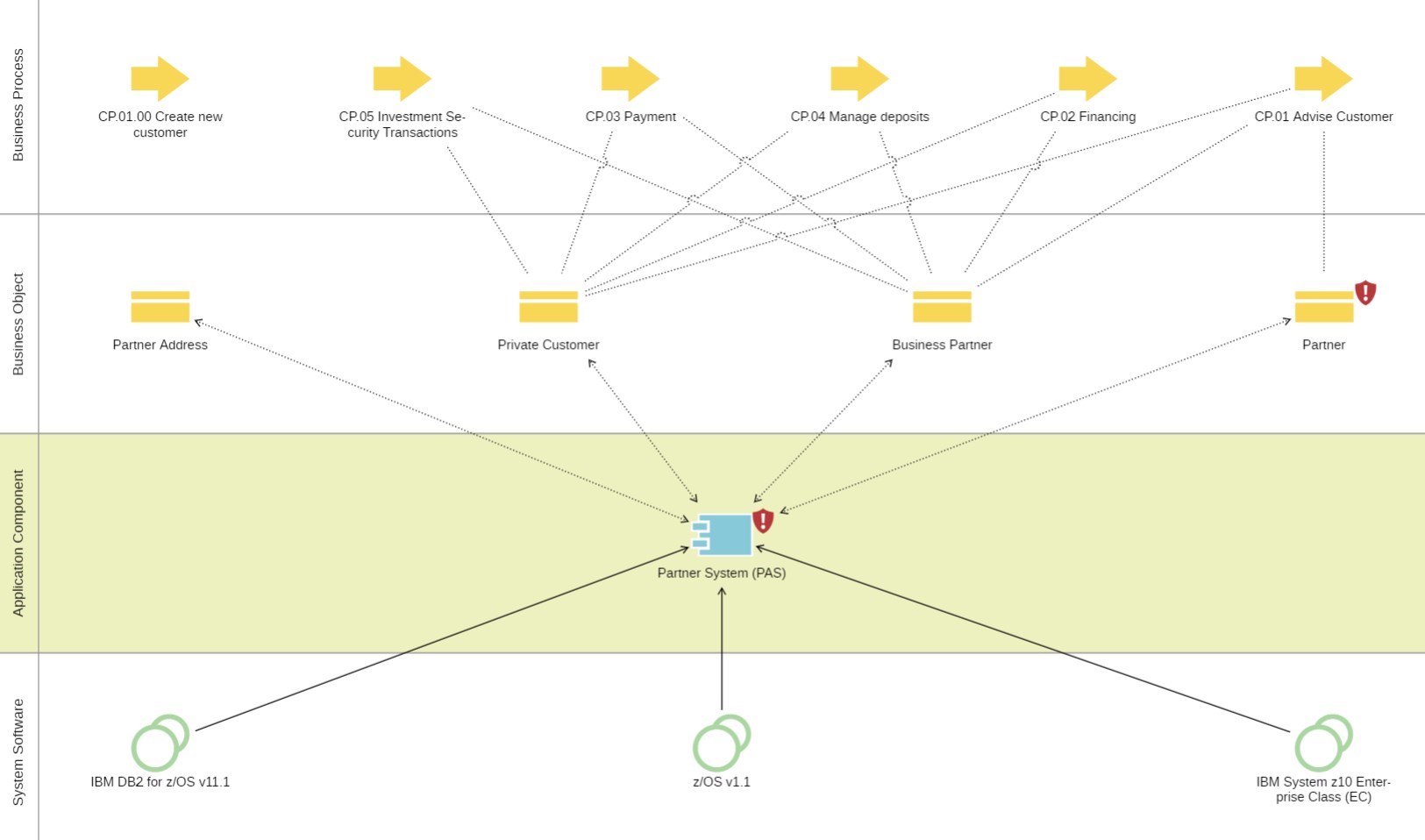
Example of a dependency diagram in the EA suite ADOIT
As a final example of an APM result type, a so-called cluster map is shown. It shows the applications and the capabilities realized by the applications. Using a so-called heatmap mechanism, the applications are colored based on the criteria defined in the application portfolio. In the concrete example, all applications with insufficient security fitness are highlighted.
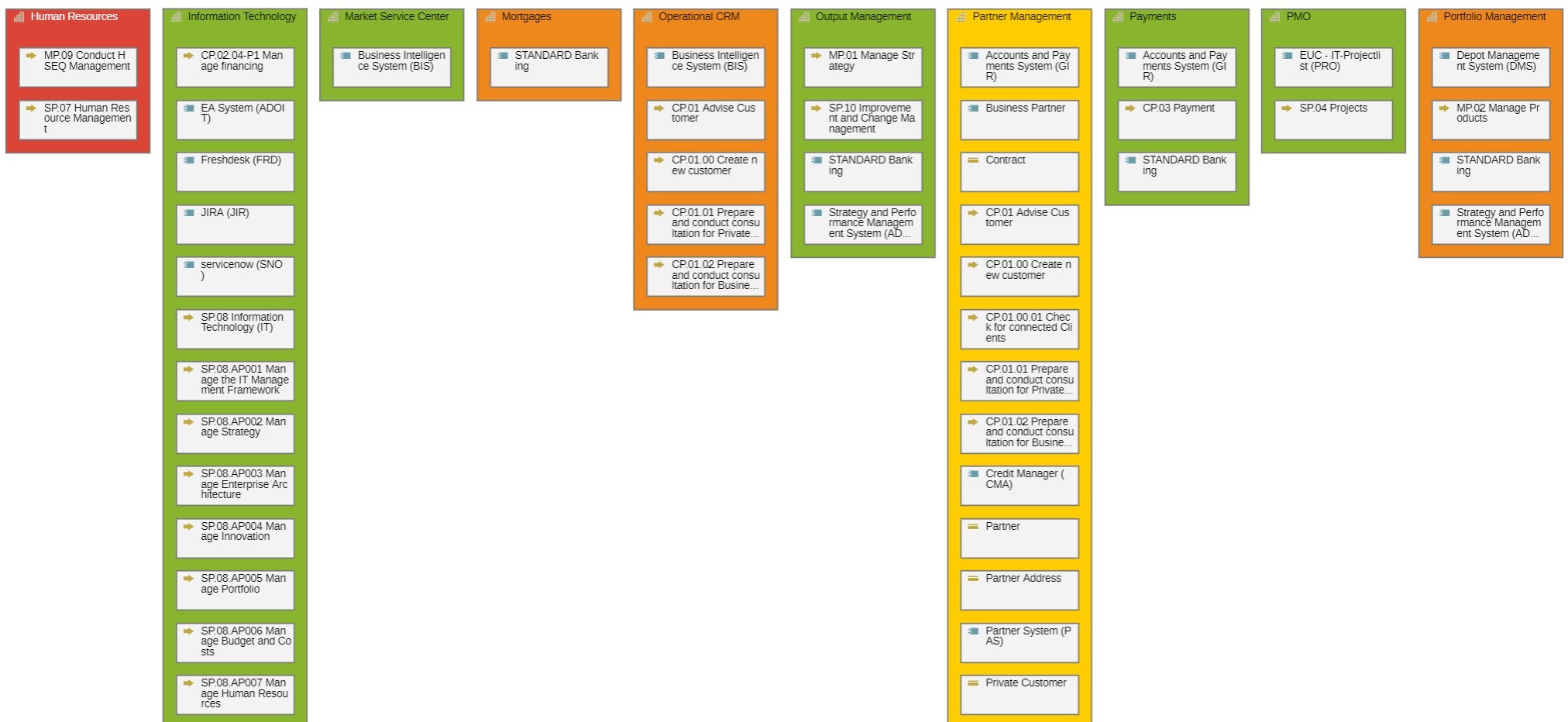
Example of a cluster map in the EA suite ADOIT
Dependencies on other EA scenarios and management disciplines.
APM provides fundamental information about applications and their dependencieson each other as well as on dependencies on other architectural elements such as business processes or system software elements. EA scenarios that benefit greatly from this or that do not function or function only to a very limited extent without this information are listed below without claiming completeness.
Capability Portfolio Management
Business Process Management
IT Cost Management
Compliance, IT Security and IT Risk Management
Business Continuity Management
Technology Portfolio Management
Business-IT Alignment
Summary
Application portfolio management is an important management and optimization tool and thus represents a central EA component in every organization. Current transformation projects, as well as other EA scenarios, also benefit greatly from a mature APM.
As one of the most important results of APM, the application portfolio is the hub of changes to the company’s application landscape, in which each application should be documented as part of the digital twin.
However, for this to happen and for the true value of APM to unfold, buy-in from application owners and all stakeholders must be solicited from the executive level. Only this way APM can live in the organization and make a significant contribution to the company’s success.
To gain an even more comprehensive understanding of application portfolio management, we recommend our free Application portfolio management e-Learning as well as our advanced resources.
Or try our latest user-centric service “Application Investment Planning” – to assess the business and IT fitness of your applications and define the most appropriate investment strategy – now with the free Enterprise architecture tool.
Browse related APM content
Sources:
1.Keller, Wolfgang. 2012. IT-Unternehmensarchitektur – Von der Geschäftsstrategie zur optimalen IT-Unterstützung . Heidelberg: dpunkt. (Seiten 35, 79)
2. Maizlish, Bryan, und Robert Handler. 2005. IT (information technology) portfolio management step-by-step: Unlocking the business value of technology. New Jersey: John Wiley & Sons.
3. Taylor, Sharon. 2007. ITIL lifecycle suite. London: The Stationery Office Ltd.
4. Walchshofer, Manuela, und René Riedl. 2017. Der Chief Digital Officer (CDO): Eine empirische Untersuchung. HMD Praxis der Wirtschaftsinformatik 54:324–337.