Introduction
In today’s digital age, cybersecurity is not just a necessity but a vital component of any organization’s operational integrity. Cyber threats are becoming more sophisticated, making traditional security measures insufficient to protect organizational assets.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework offers a structured and scalable approach to managing cybersecurity risks. The latest iteration, the NIST CSF 2.0, builds on proven practices to offer an even more robust framework.
Software suites such as ADOGRC play a crucial role in implementing comprehensive cybersecurity strategies. By conformance with NIST CSF 2.0 core functions, ADOGRC provides organizations with an advanced toolkit to enhance their security posture, streamline risk management processes, and ensure compliance with industry standards.
What is the NIST Cybersecurity Framework 2.0?
Definition and Purpose
The NIST Cybersecurity Framework (CSF) is a set of recommended practices aimed at improving cybersecurity across all sectors. The framework provides organizations with a structured and measurable approach to identifying, assessing, and managing cybersecurity risk. Designed by the National Institute of Standards and Technology (NIST), the CSF 2.0 expands on the original by introducing new best practices, standards, and guidelines.
Key aspects of the NIST CSF 2.0:
- Simplify the complexity of cybersecurity by providing a clear and concise structure to follow, which is accessible to everyone in an organization, from IT staff to executive leaders.
- Enable organizations to make informed, risk-based decisions, enhancing their ability to prevent, detect, and respond to cyber incidents.
- As globally adapted standard, it is used worldwide to protect organizations’ assets, e.g. applications, core processes, and data from cyber threats.
Components and Objectives
The NIST CSF 2.0 is structured around six main functions: Govern, Identify, Protect, Detect, Respond, and Recover. These are designed to provide a comprehensive approach to cybersecurity risk management.
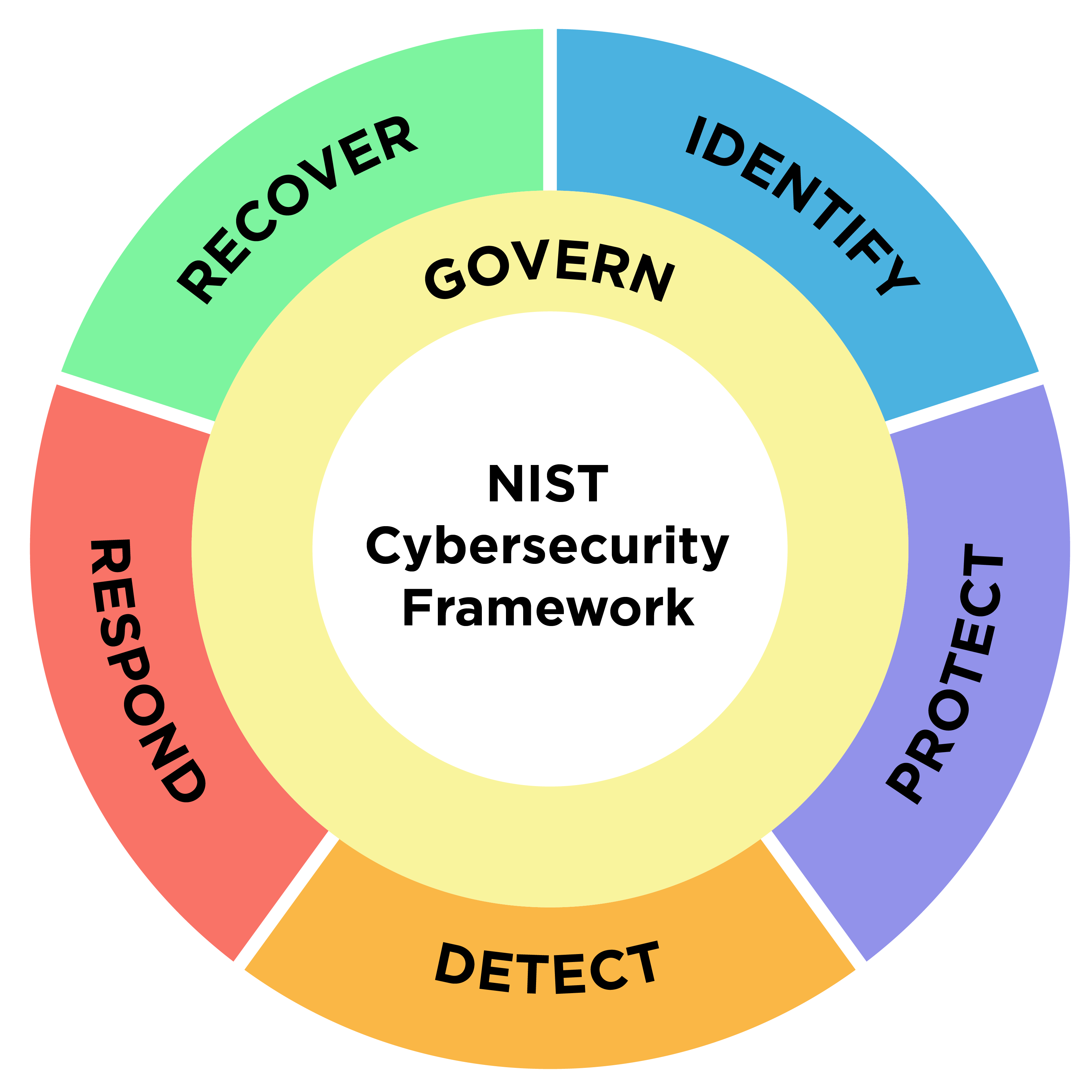
The six core functions of the NIST CSF 2.0 (credit: N. Hanacek/NIST)
Source: https://www.nist.gov/image/nist-cybersecurity-framework-20-draft
| Function | Objective |
|---|---|
| Govern | Establish, communicate, and monitor the organization’s cybersecurity risk management strategy, expectations, and policies. |
| Identify | Enhance the organization’s ability to prioritize cybersecurity initiatives by fully understanding its current risks and related assets, e.g. processes, applications and data. |
| Protect | Implement safeguards to mitigate cybersecurity risks and secure prioritized assets, e.g. core processes and applications. |
| Detect | Set up appropriate measures to ensure cybersecurity events are detected as soon as possible and properly analyzed |
| Respond | Prepare decisive actions to manage and contain detected cybersecurity incidents, utilizing strategies for incident management, analysis, mitigation, reporting, and communication. |
| Recover | Restore processes and assets affected by cybersecurity incidents promptly – aim to reduce their impact and keep communication effective and transparent. |
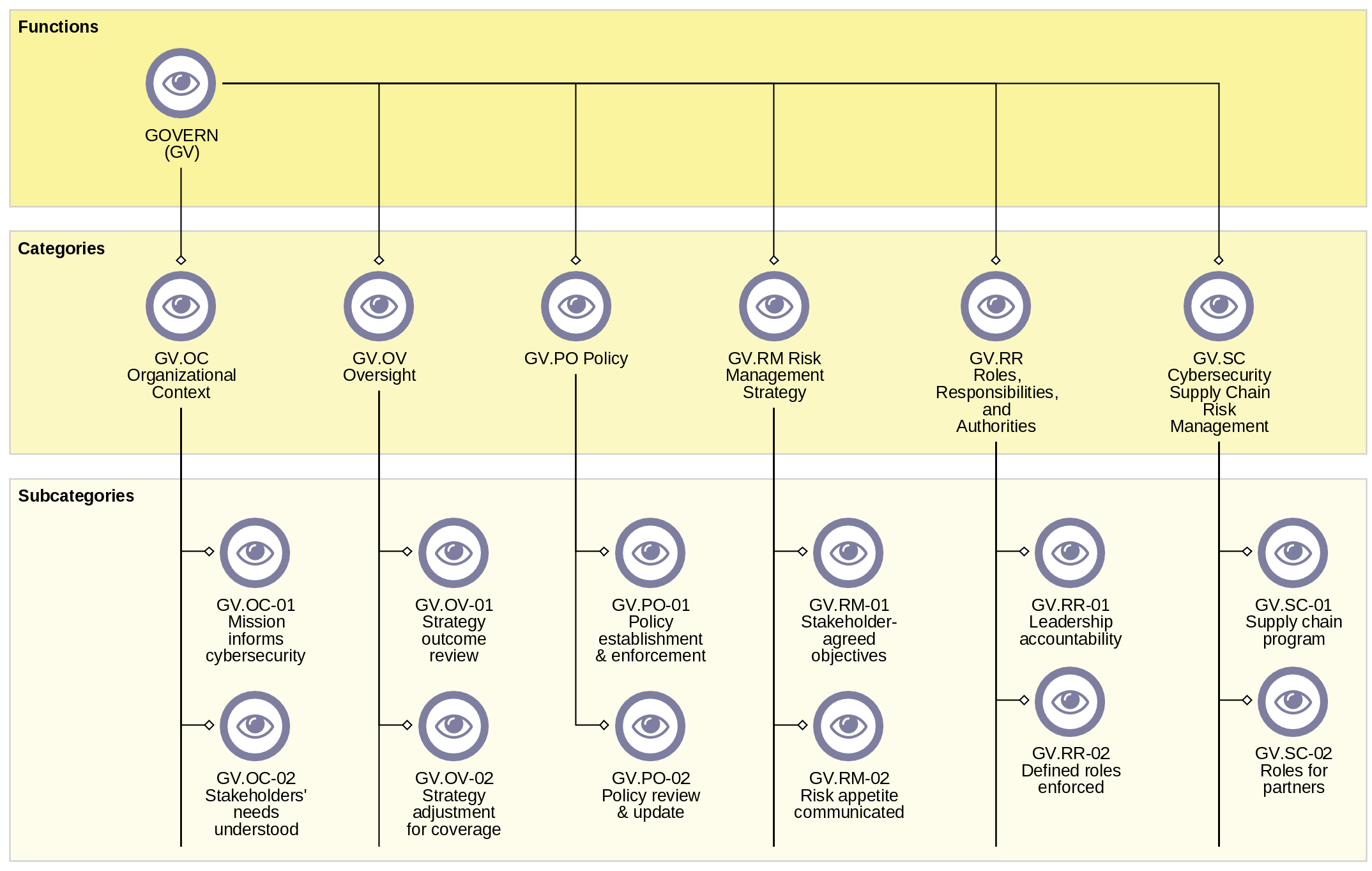
Each function is further divided into categories and subcategories, providing detailed, actionable examples for implementation. That includes and covers stakeholders, processes, inventories and catalogues as well as suggested means for communication.
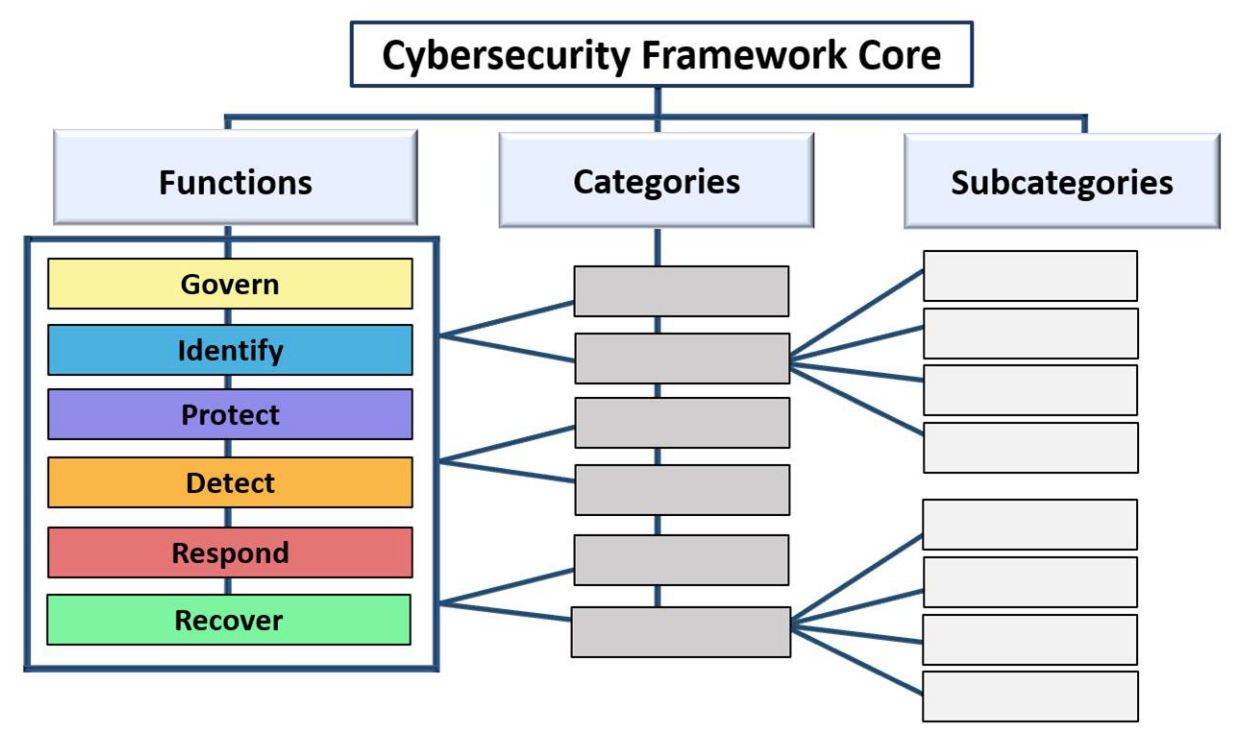
NIST CSF 2.0 Core Structure (credit: cyberframework@nist.gov)
Source: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf (Fig. 1., P. 3)
The NIST CSF 2.0 not only integrates well-established cybersecurity practices but also offers guidelines for continuous improvement, adapting to new threats and changes in technology.
Benefits of Implementing NIST CSF 2.0
The NIST CSF 2.0 encourages organizations to integrate cybersecurity risks with their overall business process management. This holistic approach ensures that security considerations are embedded at every step of business operations, providing a comprehensive view of potential vulnerabilities and enabling proactive risk management.
Key advantages:
- Unified Risk Management: Integrate cybersecurity with enterprise risks for better alignment.
- Ensure Compliance: Meet regulatory requirements with ease.
- Operational Efficiency: Optimizes processes, reducing errors, costs, and required resources.
- Increase Visibility: Improve monitoring capabilities to decrease detection and response times.
- Scalability: Automatically adapt to organizational growth and related threats.
- Security Culture: Embed cybersecurity as a fundamental business value.
Cybersecurity with ADOGRC in line with NIST CSF 2.0
ADOGRC allows any organization to achieve the cybersecurity outcomes NIST Cybersecurity Framework 2.0 strives for, utilizing its full range of features, e.g. automated workflows and revision safe histories. By design, it helps to streamline and enhance an organization’s cybersecurity practices.
- Seamless Operation: Embedding NIST CSF 2.0 functions and categories into ADOGRC allows for seamless cybersecurity management across various business processes.
- Structured Assessments: ADOGRC includes pre-configured templates conform with NIST CSF 2.0’s functions, categories and subcategories.
- Real-time Risk Analysis: Potential issues and risks become apparent, providing actionable insights through a graphical risk matrix that also includes all related assets.
- Ready-to-go Implementation Examples: Initiative pools propose implementation examples – add your parameters and start immediately.
Examples of control objectives in ADOGRC – derived from the NIST CSF 2.0 categories and subcategories of the “Govern” function
Options for tracking measures in ADOGRC that relate to the function “Govern”
Summary
The GRC suite ADOGRC facilitates companies in implementing NIST CSF 2.0 compliant cybersecurity management through proven practices and templates. The framework provides a structured basis for effective cybersecurity measures, supported by pre-configured workflows and real-time analytics. By linking risks to assets, organizations meet current security requirements and are prepared for future threats. ADOGRC optimizes and automates processes such as risk catalog management and control execution, leading to efficient task allocation within the company. The integrated authorization concept ensures the protection of sensitive information according to the need-to-know principle.